Author: admin
-
Malicious campaign targeted at Axiom.Trade users (RE-001-A)
Urgent Threat Alert: Dexiom’s Malicious Bookmark Campaign is Draining Crypto Wallets
In the ever-evolving landscape of cyber threats, a particularly insidious danger has emerged, primarily propagated through the social media platform X (formerly Twitter). Operating under the name “Dexiom,” this malicious campaign employs a clever trick: a seemingly innocent malicious bookmark that, when clicked, injects harmful code into legitimate trading platform Axiom.trade users’ browsing session, aiming to drain users’ cryptocurrency wallets.
Our recent investigations have uncovered a coordinated effort to spread this fraud. Tweets promoting “Dexiom” are easily found on X, creating a deceptive buzz that lures unsuspecting users into this sophisticated phishing scheme. You can see how widely it’s being pushed by visiting the X search results for “Dexiom”: https://x.com/search?q=dexiom&src=typed_query&f=live.
The Deceptive “Activation”: How the Bookmark Trap is Set
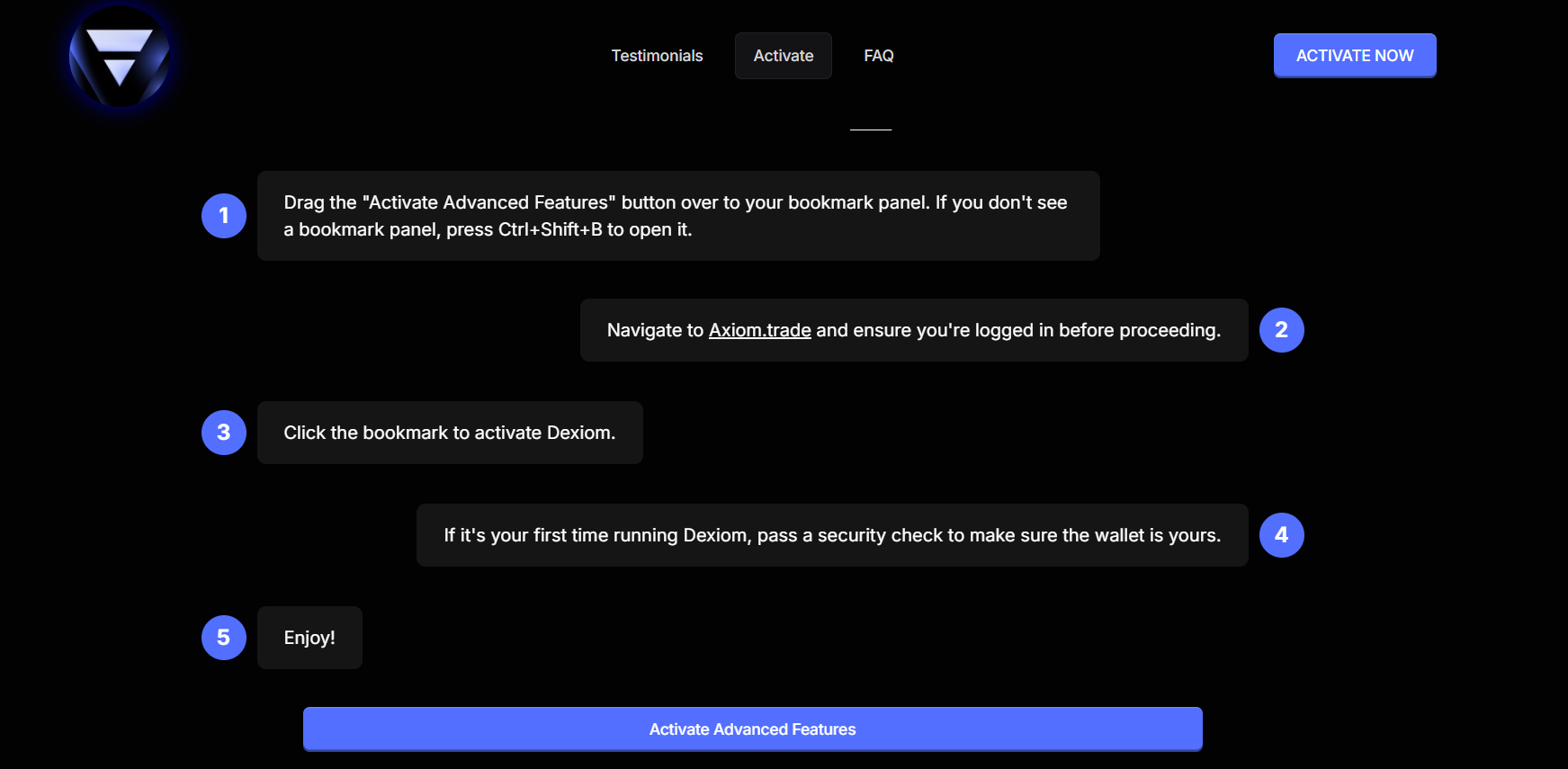
The attackers provide seemingly straightforward instructions on their websites, guiding users into activating their trap. This is how they trick you into deploying their payload:
- “Activate Advanced Features”: Users are instructed to drag a button labeled “Activate Advanced Features” directly onto their browser’s bookmark panel. If the panel isn’t visible, they’re told to press
Ctrl+Shift+Bto open it. - Navigate to Axiom.trade: The next step instructs users to go to
Axiom.trade(a legitimate platform) and ensure they’re logged into their account. This is a critical step for the attack’s success. - Click the Bookmark: Once on
Axiom.trade, users are told to click the “Activate Advanced Features” bookmark they just added, which executes malicious code. - “Security Check”: For first-time users, there’s even a “security check” step, designed to make the process appear more legitimate and ensure the wallet “belongs” to the user.
- “Enjoy!”: The final, chilling instruction.
The Hidden Danger: What the Bookmark Does
This “activate” process is far from innocent. The bookmark is actually a malicious bookmarklet – a small piece of JavaScript code disguised as a regular bookmark. When you drag it to your browser and click it while on a legitimate site like Axiom.trade, that JavaScript code is executes directly within the context of that legitimate website.
This means the attackers can:
- Bypass Browser Security: Because the code runs from your own browser, on a legitimate domain, it can often bypass typical browser security warnings and content security policies (CSPs) that would block direct phishing attempts.
- Access Your Wallet: The injected script can interact with your logged-in session on Axiom.trade, or directly with your connected crypto wallet. It can then initiate unauthorized transactions, possibly approve malicious contracts, or even attempt to extract your private keys or seed phrases, all under the guise of “advanced features.”
- Steal Funds: The ultimate goal is to get you to unwittingly approve transactions that drain your cryptocurrency holdings directly to the attacker’s wallets.
Technical Deep Dive: Under the Hood of Dexiom’s Evasion
The Dexiom campaign doesn’t just rely on social engineering; it employs sophisticated technical tactics to evade detection and frustrate analysis.
- Advanced String Obfuscation: At its core, the malicious JavaScript uses a complex string obfuscation technique. Key strings vital for its operation (like function names, element IDs, or URLs) are not stored plainly. Instead, they are referenced via numerical indices fed into a custom decoding function. This function uses a meticulously crafted internal mapping to resolve these numbers back into their original strings. This makes static analysis incredibly challenging, as human-readable terms are replaced with seemingly random numbers.
- Dynamic Junk Code and Unique Payloads: Perhaps one of the most intriguing aspects of this campaign is its use of dynamic code generation. When you visit their promotional sites, the bookmarklet payload you receive isn’t static; it contains varying amounts of “junk code” or unique elements. This means:
- Evasion of Signature-Based Detection: Each user might receive a slightly different version of the malicious JavaScript. This makes it significantly harder for antivirus software and network security tools to rely on fixed signatures to detect and block the bookmarklet.
- Frustrating Reverse Engineering: For security researchers, this dynamic junk code introduces additional hurdles. Analyzing one sample doesn’t guarantee understanding all variants, making it a more time-consuming and resource-intensive process to create universal detection rules. It can also potentially be used to track specific victim campaigns.
- Anti-Tampering and Anti-Debugging (Disabled for Analysis): The original obfuscated code included robust anti-analysis mechanisms. These were designed to detect when the script was being tampered with or run in a debugging environment (like browser developer tools). Such techniques often involve checking for modifications to built-in JavaScript functions (e.g.,
Function.prototype.toString) or detecting the presence of debugger objects, triggering infinite loops or errors to hinder reverse engineering efforts. For our analysis, these self-defending features were disabled to allow the underlying malicious logic to be observed.
Further technical details can be found over at our Github Repo here
Beyond the Bookmark: The Broader Campaign Infrastructure
The malicious bookmark is just one piece of this well-orchestrated attack. The Dexiom campaign leverages a network of deceptive domains, all designed to appear legitimate and distribute the bookmarklet:
https://dexiom.space/(ghostarchive: https://ghostarchive.org/archive/dAzHr)https://dexiomtools.pro/(ghostarchive: https://ghostarchive.org/archive/WvNhA)https://dexiom.tools/(ghostarchive: https://ghostarchive.org/archive/YbxAQ, .warc file: contact us)https://dexiom.app/(ghostarchive: https://ghostarchive.org/archive/mnxAC)https://dexiom.trade/(ghostarchive: https://ghostarchive.org/archive/XRRxU)https://dexiom.icu/(ghostarchive: https://ghostarchive.org/archive/A8cLR, .warc file: contact us)https://dexiom.live/https://dexiom.org/(ghostarchive: https://ghostarchive.org/archive/0A4uQ)https://dexiom.pro/(ghostarchive: https://ghostarchive.org/archive/y0GGa)
These domains serve as the initial lure, hosting the instructions for the bookmarklet
Protecting Your Digital Assets: Don’t Fall for the Bookmark Trick
Given the active and technically advanced nature of this campaign, extreme vigilance is critical. Here are essential steps to protect yourself and your crypto:
- Never Drag Unknown Bookmarks: This is the golden rule for bookmarklet attacks. If you don’t know exactly what JavaScript code a bookmark contains (you can inspect it by right-clicking and editing it), do NOT drag it to your browser or click it.
- Verify All Links and Websites Meticulously: Always manually type the URLs of legitimate platforms like axiom.trade. Never click links from suspicious tweets, emails, or messages. Phishing sites often have subtle misspellings or use uncommon top-level domains.
- Regularly Inspect Browser Extensions & Bookmarks: Review your browser’s extensions and bookmarks periodically. Remove anything you don’t recognize or explicitly remember installing. Malicious bookmarklets can hide in plain sight.
- Enable Multi-Factor Authentication (MFA): Use MFA on all your cryptocurrency exchanges, wallets, and related services for an added layer of security.
- Use Hardware Wallets: For significant crypto holdings, a hardware wallet provides the strongest defense against software-based attacks, as your private keys never leave the device.
- Be Skeptical of “Too Good to Be True” Offers: Promises of “advanced features,” unrealistic returns, or exclusive access that require unusual setup steps are almost always a red flag for scams.
- Educate Yourself Continuously: Stay informed about common phishing tactics, new cyber threats, and the latest security best practices. Follow reputable cybersecurity news sources.
- Report Suspicious Activity: If you encounter tweets or websites promoting Dexiom or similar suspicious activities, report them immediately to X, your browser vendor, and relevant cybersecurity authorities.
The Dexiom campaign, with its cunning bookmarklet vector and anti-analysis techniques, is a stark reminder that cybercriminals are constantly innovating. By understanding their methods and practicing robust cybersecurity hygiene, you can significantly reduce your risk of falling victim to these sophisticated schemes. Stay safe online!
- “Activate Advanced Features”: Users are instructed to drag a button labeled “Activate Advanced Features” directly onto their browser’s bookmark panel. If the panel isn’t visible, they’re told to press